What is a cryptographically secured distributed ledger?
A cryptographically secured distributed ledger is a type of database that is:
- Distributed—It’s shared across multiple computers (called nodes) rather than being stored in a single central server. Each participant holds a copy of the ledger.
- Ledger—It records transactions or data entries in a chronological and append-only fashion (new data is added, but past data is not easily altered).
- Cryptographically secured—It uses cryptographic techniques (like hashing, digital signatures, and public/private key encryption) to:
- Ensure integrity: Each block or record is linked to the previous one with a cryptographic hash, making tampering easily detectable.
- Provide authentication: Transactions are signed with private keys so only authorized parties can add valid entries.
- Maintain trust without a central authority: The security comes from mathematics and distributed consensus, not from trusting a single institution.
👉 The most well-known example of such a system is blockchain, which underlies cryptocurrencies like Bitcoin and Ethereum. However, distributed ledgers can exist without being blockchains (for example, directed acyclic graphs like IOTA).
Let’s walk through how cryptography secures a distributed ledger step by step.
1. Hashing for Integrity
- Every transaction (or block of transactions) is passed through a hash function (e.g., SHA-256).
- A hash is like a digital fingerprint: unique, fixed-length, and impossible to reverse-engineer.
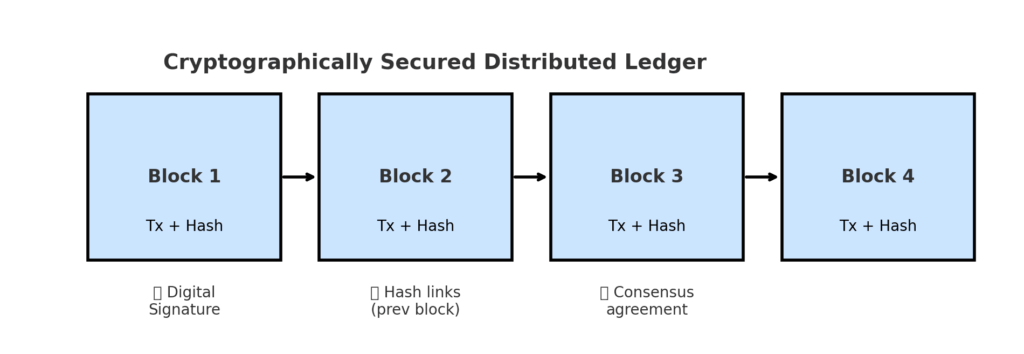
- Each new block contains the hash of the previous block → forming a chain.
- If anyone tries to change past data, the hash breaks, alerting the network immediately.
📌 Example:
Block 5 includes:
- Its own transaction data
- The hash of Block 4
→ If Block 4 is altered, Block 5’s hash no longer matches.
2. Digital Signatures for Authentication
- Users have a private key (secret) and a public key (shared).
- When a user submits a transaction, they digitally sign it with their private key.
- Anyone can verify the signature with the public key, proving:
- The transaction really came from that user.
- The transaction wasn’t altered after being signed.
📌 This prevents fake transactions (e.g., pretending to send money from someone else’s account).
3. Consensus for Agreement
Since the ledger is distributed across many computers, all copies must agree on the “true” state. Cryptography supports consensus mechanisms, such as:
- Proof of Work (PoW): Nodes solve cryptographic puzzles; the winner adds the next block.
- Proof of Stake (PoS): Validators “stake” coins; they are chosen randomly to validate and secure the chain.
- Others (PBFT, PoA, DAG-based, etc.).
📌 Without consensus, someone could try a “double-spend” (using the same coin twice). Consensus ensures only one valid version survives.
4. Immutability
- Once blocks are linked with hashes + validated by consensus, altering the past would require re-doing all cryptographic proofs across the majority of the network.
- This makes tampering computationally or economically infeasible.
✅ In summary:
- Hashes → Protect integrity of the chain.
- Digital Signatures → Ensure authenticity of transactions.
- Consensus → Makes sure all participants agree on a single truth.
- Together, these make the ledger trustless, tamper-resistant, and secure without needing a central authority.
Let’s use a real-world analogy to make this less abstract.
Imagine a shared notebook in a big classroom:
- Distributed Ledger = Shared Notebook
- Everyone in the class has their own identical copy of the notebook.
- Whenever something is written, all copies must match.
- Hashing = Page Number + Tamper Seal
- Each page not only has a page number but also a stamp (a hash) that depends on the contents of the page.
- At the top of each new page, you also write down the stamp from the previous page.
- If anyone tries to erase or change a word on Page 12, its stamp changes → Page 13’s stamp doesn’t match anymore → the whole notebook after Page 12 is obviously wrong.
- Digital Signatures = Handwritten Signatures
- When you add something to the notebook, you must sign it with your unique signature (private key).
- Everyone can check your signature against your public handwriting sample (public key) to confirm it’s really you.
- This prevents classmates from writing entries pretending to be you.
- Consensus = Class Voting Rules
- The class needs to agree which entries are valid.
- Rule example: the first student who solves a hard math puzzle (Proof of Work) gets to write the next page.
- Or: students who deposited their allowance (stake) get randomly chosen to write (proof of stake).
- Everyone else checks their work before accepting it into their notebook.
- Immutability = Cemented Pages
- Once the page is stamped, signed, and approved by the class, it’s like sealing it with superglue.
- You can’t rip it out or change it without the entire class noticing—and you’d need to re-glue every page after it, which is practically impossible.
✅ End result:
The notebook (distributed ledger) becomes secure, transparent, and tamper-resistant without needing a teacher (central authority) to guard it. Trust comes from the system itself, not from one person.